Encryption does not itself prevent interference but denies the intelligible content to a would be interceptor. End to end encryption is the most secure way to communicate privately and securely online.

Public Key Cryptography Wikipedia
Say i have some data and a password and i want to encrypt the data in such a way that it can only be recovered with the right password.
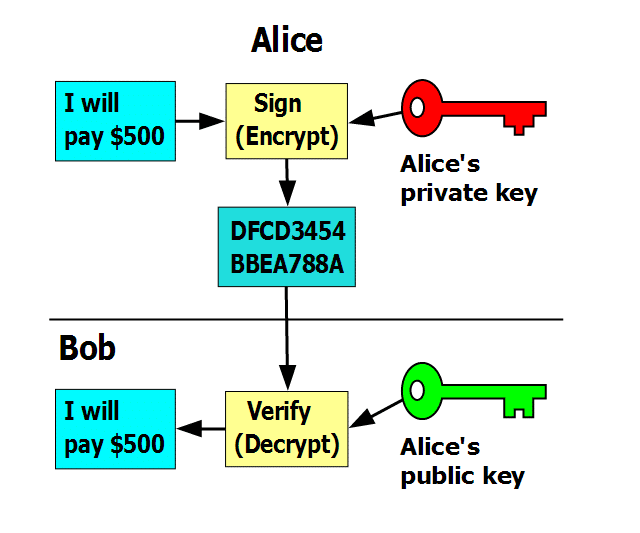
How does encryption work. Hes also a keen linux user who loves to prototype and come up with new creations. Protecting amazon sqs data using server side encryption sse and aws kms server side encryption sse lets you transmit sensitive data in encrypted queues. Https is simply your standard http protocol slathered with a generous layer of delicious ssltls encryption goodness.
How to implement this. In an encryption scheme the intended information or message referred to as plaintext is encrypted using. Join us for a quick history lesson and learn more about how encryption works.
Unless something goes horribly wrong and it can it prevents people like the infamous eve from viewing or modifying the requests that make up your browsing experience. Techworld looks to explain what encryption is and how it works. The data is simply encoded before being written or decoded before being read.
Encryption has a long history dating back to when the ancient greeks and romans sent secret messages by substituting letters only decipherable with a secret key. Aman is a java programmer who works on projects related to jsp web hosting and virtual servers. In its most basic form encryption is the process of encoding data making it unintelligible and scrambled.
Think of encryption as an adapter. The only difference is that a key is passed at some point usually when the drivedriver is initialized to be used for the encryptiondecryption. For many the word encryption probably stirs up james bond esque images of a villain with a briefcase handcuffed to his wrist with nuclear launch codes or some other action movie staple.
In cryptography encryption is the process of encoding a message or information in such a way that only authorized parties can access it and those who are not authorized cannot. How does this technically work ie. By encrypting messages at both ends of a conversation end to end encryption prevents anyone in the middle from reading private communications.
In a lot of cases encrypted data is also paired with an encryption key and only those that possess the key will be able to open it.
Camsoft Cyber Security Infographics How Does Encryption Work And

Huh Cryptocurrencies Cryptography How Does It All Work
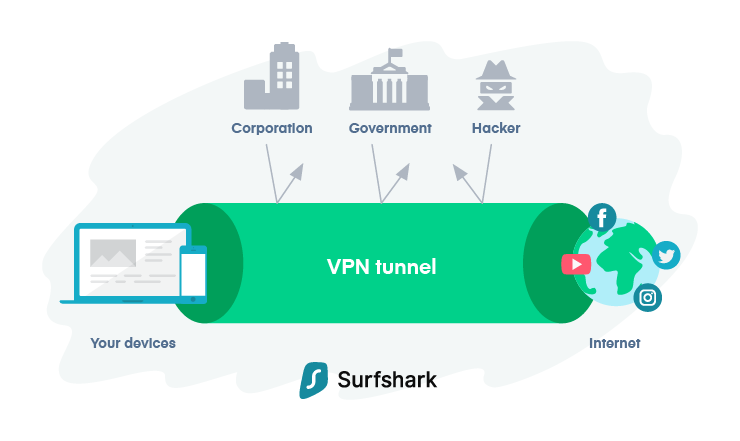
Vpn Encryption Surfshark