Ever since i wrote about the 34000 myspace passwords i analyzed people have been asking how to choose secure passwords. A reporter chronicles what its like to get by without using or accessing a single product from amazon apple facebook google and microsoft for one week reporter kashmir hill spent six weeks blocking amazon facebook google microsoft and apple from getting her money data and attention using a custom built vpn.
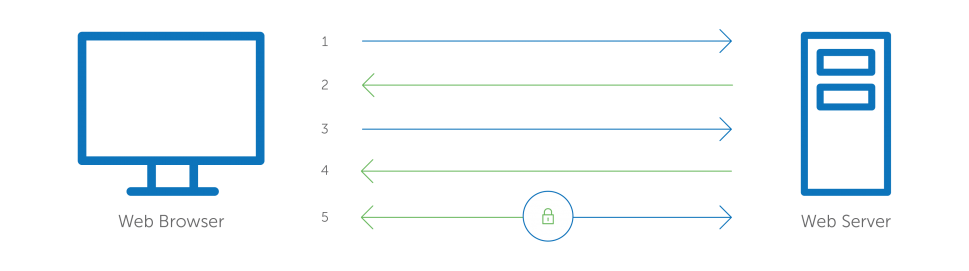
What Is Ssl Secure Sockets Layer Digicert Com
A practical attack against mdm solutions.

How does encryption work why is it considered a premier tool in it security. Bibme free bibliography citation maker mla apa chicago harvard. If you need more instances complete the amazon ec2 instance request form with your use case and your instance increase will be considered. Theinquirer publishes daily news reviews on the latest gadgets and devices and inqdepth articles for tech buffs and hobbyists.
Limit increases are tied to the region they were requested for. Note that cc28xlarge hs18xlarge cr18xlarge g2 d2 and i2 instances are not available in all regions. News analysis and commentary on information technology trends including cloud computing devops data analytics it leadership cybersecurity and it infrastructure.
Spyphones are surveillance tools surreptitiously planted on a users handheld device. Why does the open source repository contain code specific to the commercial version of mattermost the commercial version of mattermost is designed to never lock in your data. Security is a top priority for e commerce giant shopify with over 600000 businesses in 175 countries trusting them to sell online and everywhere in the world.
While malicious mobile applications mainly phone fraud applications distributed through common application channels target the typical consumer spyphones are nation states tool of attacks.
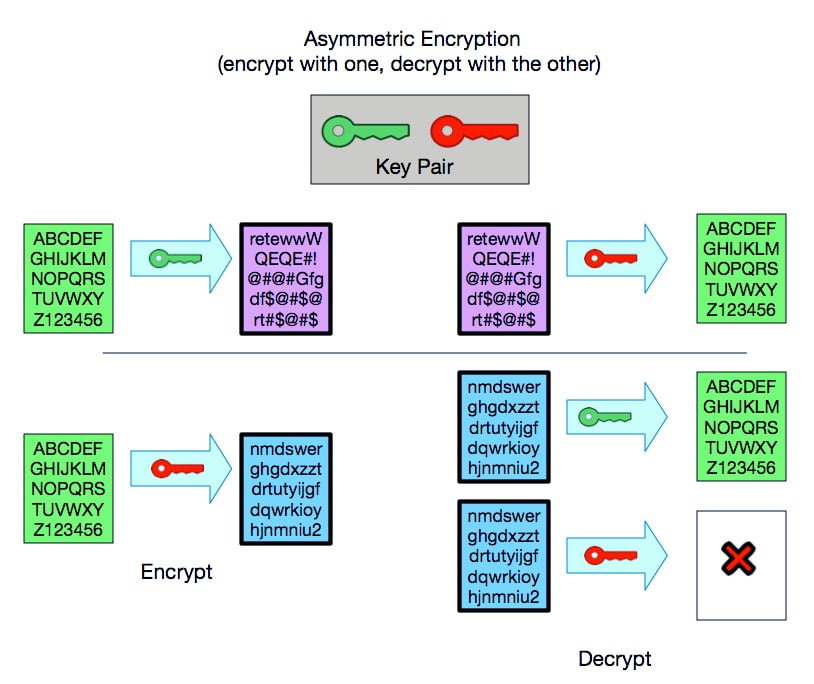
Understanding Digital Certificates And Code Signing

Manage Encryption With Adobe Enterprise

Encryption Key Management Box Keysafe