Data encryption techniques since youre interested in encryption maybe youd like these. Aman is a java programmer who works on projects related to jsp web hosting and virtual servers.

Public Key Cryptography
Microsoft net a billion dollar boondoggle.

How does asymmetric encryption work. Hes also a keen linux user who loves to prototype and come up with new creations. While each has specific uses a robust communications encryption solution will typically implement all three. Join us for a quick history lesson and learn more about how encryption works.
Rsa rivestshamiradleman is one of the first public key cryptosystems and is widely used for secure data transmission. Learn about asymmetric encryption symmetric encryption key strength public key encryption pre shared key encryption and how it all fits together. Public key or asymmetric encryption uses the recipients public key as well as a mathematically matching private key.
Https is simply your standard http protocol slathered with a generous layer of delicious ssltls encryption goodness. Electronic mail is a natural and perhaps inevitable use of networked communication technology that developed along with the evolution of the internetindeed message exchange in one form or another has existed from the early days of timesharing computers. In such a cryptosystem the encryption key is public and it is different from the decryption key which is kept secret private.
In rsa this asymmetry is based on the practical difficulty of the factorization of the product of two large prime numbers the factoring. This is a survival guide covering the mind numbing topics of cryptography encryption authorization and authentication. Symmetric encryption algorithms.
Encryption has a long history dating back to when the ancient greeks and romans sent secret messages by substituting letters only decipherable with a secret key. Unless something goes horribly wrong and it can it prevents people like the infamous eve from viewing or modifying the requests that make up your browsing experience. For example if joe and karen both had keys to a box with joe having the public key and karen having a matching private key joe could use his key to unlock the box and put things into it but he wouldnt be able to view items already in there nor would he be.
Epa is lying to us. Survival guide encryption authentication. A fundamental topic of it security that often gives people difficulty is understanding the difference between symmetric asymmetric encryption and hashing.

Public Key Cryptography Solved An Age Old Encryption Problem
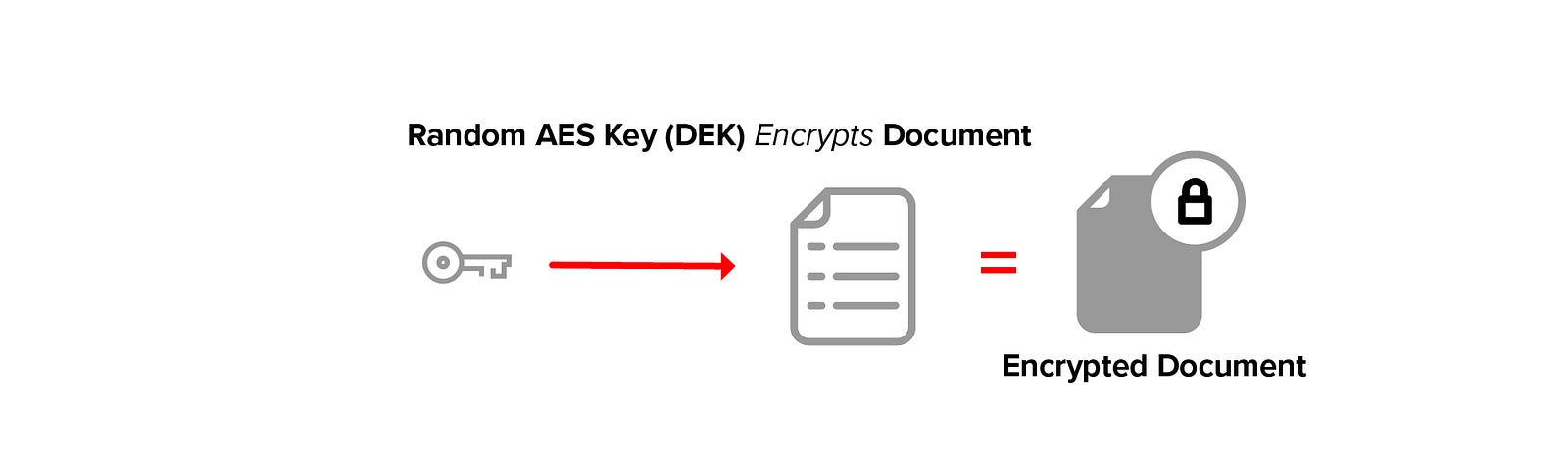
Open The Envelope The Salty Hash

A Deep Dive On End To End Encryption How Do Public Key Encryption